What’s the deal? I’m testing using https://coveryourtracks.eff.org/ Is it truly unique (and repeatable), or is it perhaps being randomized on every request?
I’ve tried normal Firefox, Mull, and IronFox. With and without jShelter.
I’m using my phone. Stock Android on a Pixel 7 Pro.
In DDG Browser I have a “nearly unique” fingerprint.
I installed CanvasBlocker and disabled privacy.resistFingerprinting in IronFox (since CanvasBlocker said to), and my fingerprint is still unique. I guess I’m not surprised since I think CanvasBlocker is designed to randomize canvas fingerprinting.
Any tips on having even a shred of privacy when browsing the web on Android?
Update
The biggest identifying characteristics are screen size and user agent. User agent can be faked with an extension. I can’t exactly change my screen size.
I don’t know what exactly what I did, but I managed to improve to “nearly unique” in IronFox. I think all I did was install Cookie Autodelete. It’s an extension I’ve used for a long time in Mull, and finally got around to installing it. Then I installed “User-agent Switcher” and chose a Chrome user-agent and now I’m back to “Unique”. 🤔
EFF mentioned Tor Browser having some other best anti-fingerprinting, so I tried installing that. “Unique Fingerprint”. Again, maybe that’s fine if it means it’s randomized on every request. Does anyone know if that’s the case? If part of the fingerprint is a hash of canvas data and WebGL data, etc. Then I can easily see your fingerprint being unique if a browser or an extension is intentionally fuzzing that data.
Update 2
I tried Fennec with just jShelter, uBlock Origin, and Cookie AutoDelete (not that I think those last two matter).
Obtained a “randomized fingerprint” result. Success?
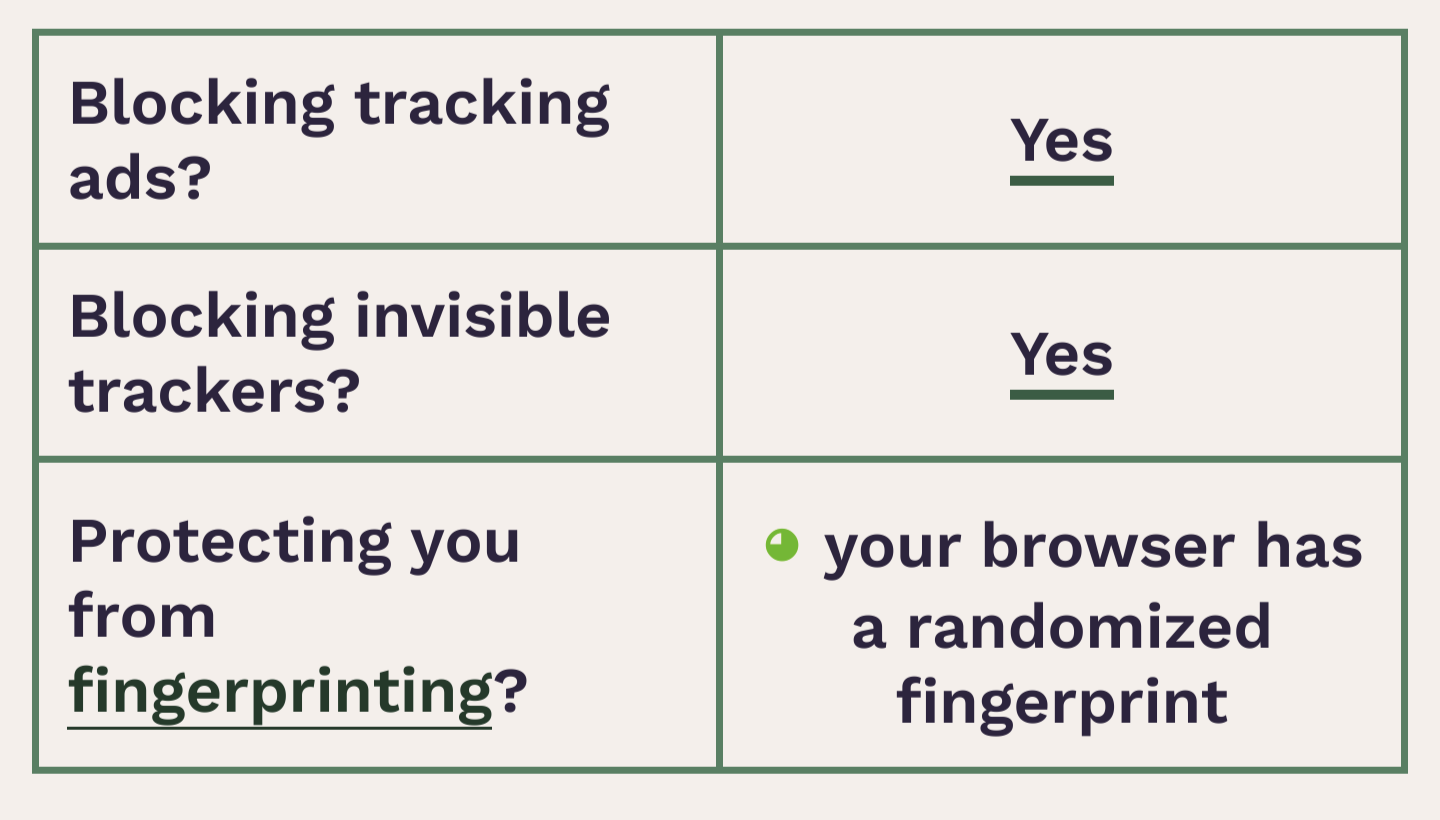
scroll down and see which fingerprinting parameter gives you away
Protip: if your fingerprint changes every 30 seconds, then you’ve defeated their being able to track you with fingerprinting.
Install the Chameleon extension.
This isn’t as simple or successful as you make it out to be, which is why tor opts for normalization instead of randomization. There are like hundreds of variables with billions of permutations in a browser, and some combinations never appear together in the real world. If all the major vars indicate Firefox 136, but your user agent is Chrome 98, and your language is English but location is Portugal, and some of those are changing every 30 seconds, you could end up being more unique and easier to track than if you’d just used mullvad or arkenfox. Browsers and trackers constantly evolve, so you can’t ever really know how effective any random combination truly is.
Chameleon changes much more than just the user agent. We have no evidence to suggest that they can link your changing fingerprints. Thats the point. Its a fingerprint.
If you rub sanding paper on your computer you can get rid of fingerprints I hope this helps
Linux x86_64
Hmm. 1 in 6 browsers checked at that site have this value. I’m sure your typical linux user is a little more privacy aware but that’s still an impressive ratio when the overall linux desktop usage is usually pegged between 4% and 5%.
Android shows up as Linux
And scrapers/bots. These make up a staggering amount of web traffic and Linux dominates server land.
Bots are likely going be either special user agents or common ones like Windows
We had to write a classifier for web traffic at a prior employer using known scraper IPs as our training set, and Chrome on Linux got us over 70% of the way there. A sizable number of bots that are just a $5 a month Linux based VPS with selenium and chrome engine.
Why is it so hard to not be fingerprinted. Surly if everyone generated enough noise then it would be impossible?
Thing is most people just don’t care, and don’t understand it. Also, it turns out it’s really easy to fingerprint people. Your list of installed fonts alone is enough to fingerprint you in many cases, and it’s easy to figure out your entire list of installed fonts with JavaScript.
Add a few more data points like screen size and resolution, user-agent, and you can fingerprint 90% of people. And if that’s not enough, every device—even individual video cards of the same model—renders an HTML canvas differently enough that it’s detectable.
It turns out it’s very hard to not be completely unique when you add all the up.
I feel like it should be a crime to do fingerprinting like this, and to grab and store the browsing habits of every citizen for their whole life, but this is America (for me), and it’s never going to change.
Stop trying to avoid having a unique fingerprint that’s basically impossible unless you use Mullvad Browser or Tor.
https://github.com/arkenfox/user.js/wiki/3.3-Overrides-[To-RFP-or-Not]#-fingerprinting





